Role-Based Access Control
Overview
Role-Based Access Control (RBAC) is a permission management system that restricts access to Fivetran resources based on user roles. Each user is assigned a role that determines what they can view or manage. RBAC ensures users only have access to the resources relevant to their responsibilities.
In our RBAC model, we provide a set of standard and custom roles to grant or deny access to various Fivetran resources within an account:
Activations permissions are managed through Workspaces, separate from the Fivetran RBAC model. While all users can view the Activations tab, you must request workspace access from the Owners of the workspace or a Fivetran Account Administrator to use it. Learn more in our Workspaces documentation.
User roles also manage permissions for related areas of each resource, like the External logging services and Transformations for the Destinations resource.
Our RBAC model introduces the following features:
- Teams let you scale role and permission management across a large number of employees easily, while not affecting an individual employee's role and permissions. Delegating permissions from account-level user and team roles to users and teams — scoped per destination or connection — along with support for custom role creation and assignment.
- The Destination Creator and Create Connection roles automatically give you and your team members control over the destinations or connections you or your team create. This access automation lets you eliminate any waiting time for the approval by the central data team and independently manage access permissions for the resource right after its creation.
RBAC model benefits
For enterprise customers, a typical team structure might look like this:
- A core data team manages a central destination within the organization's Fivetran account.
- One or more teams manage centralized destinations, such as Snowflake, and are responsible for the data that lands in the destinations.
- One or several project or operational teams need to manage their specific data sources.
RBAC supports this typical team structure by offering flexibility in how roles and permissions are granted and delegated:
- Fast access - Project and operational teams get immediate access to the data they need - without delays caused by dependencies on core data teams.
- Reduced burden - Centralized teams avoid the overhead of manually managing access requests.
- Granular control - Permissions can be precisely scoped to meet enterprise compliance and security requirements.
Standard roles in our RBAC model
Fivetran’s RBAC model supports fine-grained, hierarchical access control across three main resource types, listed from highest to lowest:
- Account - Account-level roles grant permissions to manage all destinations and connections.
- Destination - Destination-level roles allow control over a specific destination and its connections.
- Connections - Connection-level roles only provide permissions for specific connections.
Roles assigned at a higher level cascade down to lower levels. For example, an account-level role may include permissions to manage all destinations and connections, whereas a connection-level role cannot access account-level settings.
For a user to have access to all destinations, assign an account-level role with the necessary permissions. For a user needing access to a specific destination and its connections, set a destination-level role.
The following table lists the user roles in our RBAC model:
| Current RBAC Model User Role | Legacy RBAC Model User Role | Description |
|---|---|---|
| Account Administrator | Owner | View and edit account information, including billing, usage, users, roles, API access, and security settings. Create, view, edit, and delete destinations and connections. Create, view, edit, and delete transformations and manage external logging services. Register HVR hub system. |
| Account Billing | Billing | View billing and usage information. Cannot edit security settings, users, roles, destinations, and connections. |
| Account Analyst | N/A | View the list of destinations and users in the account. View destinations and view, create, edit and delete transformations. Create, view, edit, and delete connections. Cannot edit account information. Cannot create, edit, or delete destinations. |
| Account Reviewer | Read Only | View account information, destinations, and connections. Cannot edit account information. Cannot create, edit, or delete destinations and connections. |
| Destination Creator | N/A | Create new destinations. Cannot view, edit, or delete existing destinations. Cannot create, view, edit, or delete connections. Cannot edit account information. Destination Creators are Destination Administrators in destinations they created. |
| Manage Destination | Destination Administrator | View, edit, and delete destinations. Create, view, edit, and delete connections. Create, view, edit, and delete transformations and manage external logging services. Cannot edit account information. |
| Edit Destination | Destination Analyst | View destinations. Create, view, edit, and delete connections. Create, view, edit, and delete transformations. Cannot edit account information. |
| View Destination | Destination Reviewer | View the destinations that you are invited to and their associated connections. Cannot create, edit, or delete destinations or connections. Cannot edit account information. |
| Create Connection | Connection Creator | Create, view, edit, and delete connections. View destinations in which this role is assigned. Cannot create, edit, or delete destinations. Cannot edit account information. Connection Creators have the Manage Connection role for the connections they created. |
| Manage Connection* | Connection Administrator | View, edit, and delete connections. Cannot create new connections. Cannot create, view, edit, and delete destinations. Cannot edit account information. |
| Edit Connection* | Connection Collaborator | View and edit connections assigned to the role. Cannot create or delete connections. Cannot view, create, edit, and delete destinations. Cannot edit account information. |
| View Connection* | Connection Reviewer | View connections assigned to the role. Cannot create, edit, or delete connections. Cannot create, view, edit, or delete destinations. Cannot edit account information. |
See our Role Permission Matrix Tables documentation for more details on the permissions each standard role provides.
*These roles are only available on the Enterprise or Business Critical plan.
You can only use account-level roles with Fivetran SCIM user provisioning. Destination-level or connection-level roles are not supported in the Fivetran SCIM API.
How our RBAC model works
Our RBAC model works as follows:
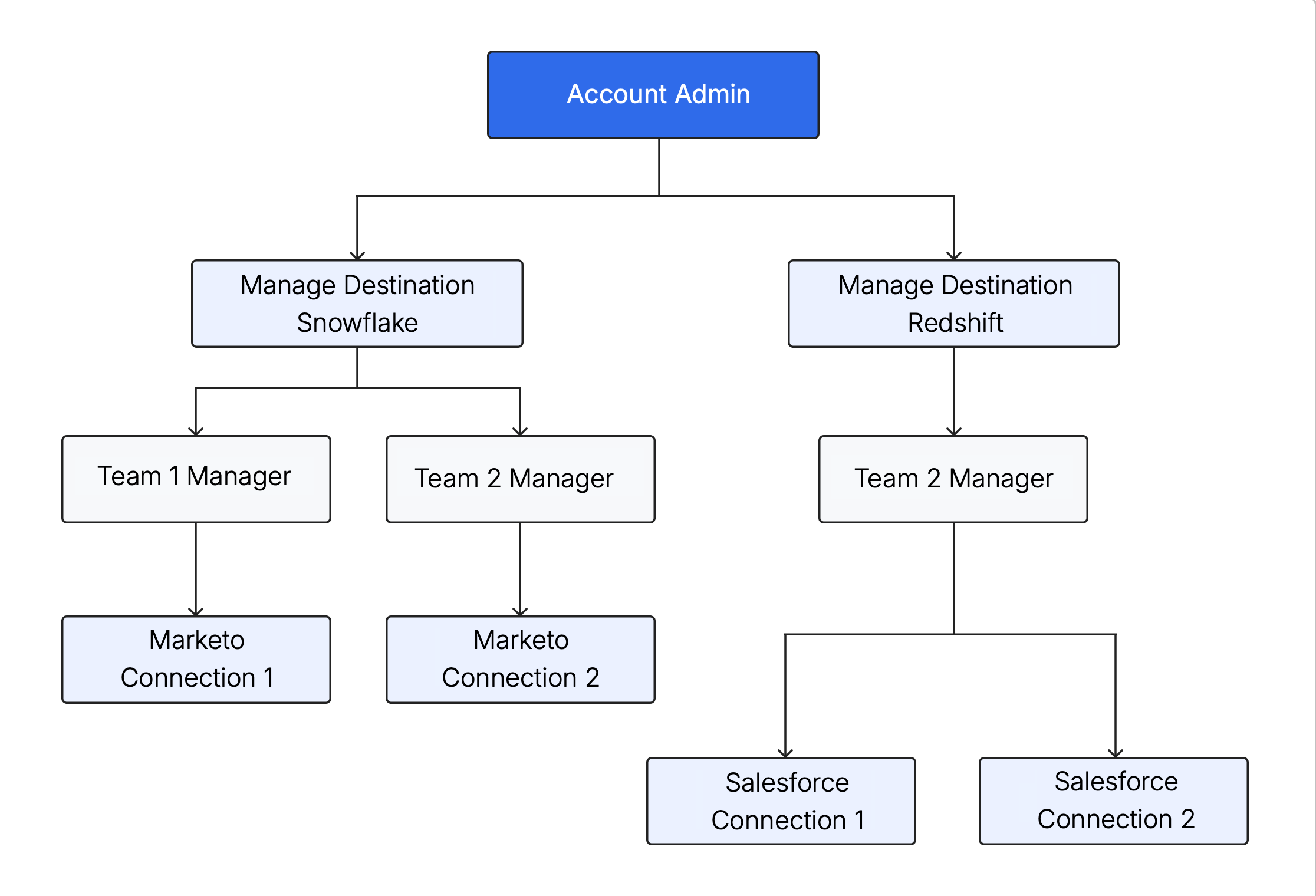
- Account administrators manage the entire account. They add users with the Destination Creator or Manage Destination role for existing destinations.
- Users with the Destination Creator role can create and manage destinations they add.
- Any user with the Manage Destination role can add teams that need to sync data to the destination.
- Each team has a team manager who adds users to the team as team members, or remove them from the team.
- Team roles in account, destinations, and connections allow delegating permissions in the corresponding resources in the same way as user roles do. This means that teams also don't have to rely on users with Manage Destination or Account Administrator roles to manage memberships. In turn, users with the Manage Destination role don't have to rely on Account Administrators to create destinations or add teams.
How we recommend using our RBAC model
Account permissions
- Get a list of users who need access to the entire account.
- Set up a team and add these users to the team.
- Set the team's role to Account Administrators.
We recommend having at least two Account Administrators at all times. A single Account Administrator may be locked out due to a potential security breach, or be unavailable when, for example, a role needs to be assigned or unassigned.
Destination permissions
- Get a list of users who need to set up their own destinations.
- Map the list of destinations to the list of users who need to manage it.
- Create a team per destination or a set of destinations.
- Assign the team to each of those destinations.
We recommend having at least two users with the Manage Destination role at all times. A single user may be locked out due to a potential security breach, or be unavailable when, for example, a destination needs to be edited or deleted).
Connection permissions
- Get a list of connections syncing data to Fivetran.
- Get a list of teams who own those connections and map them out.
- Get a list of managers for those teams.
- Set up teams and associate connection level permissions.
We recommend having one team with the Manage Connection role per connection. If a user from another team needs to be added, that individual user can be added to the team that manages the connection.
Custom roles in our RBAC model
If you're on the Enterprise or Business Critical plan, in addition to our standard roles, you also can create and manage custom roles that allow modifying both the access scope and resource area permissions.
RBAC permissions
The following table describes the permissions we use in our RBAC model:
| Permission | Description |
|---|---|
| View | Allows user to view the relevant resource areas. Applicable for:
|
| Create | Allows users to create and then view and manage only those objects of the relevant resource areas they created. Applicable for:
|
| Edit | Allows user to edit and view objects of the relevant resource areas. Applicable for:
|
| Manage | Allows user to view, create, edit, and delete objects of the relevant resource areas. Applicable for:
|
| None | Disables user's access to objects in the relevant resource area. Applicable for:
|
The following tables show the list of permissions used for each resource area.
Account permissions
| Resource area | Permissions |
|---|---|
| Settings | Edit, View, None |
| Billing | Edit, View, None |
| Roles | Manage, View, None |
| Users | Manage, None |
Destination permissions
| Resource area | Permissions |
|---|---|
| Destinations | Manage, Create*, Edit, View |
| Users | Manage, None |
| External logging services | Manage, None |
| Transformations | Manage, View, None |
*The custom role must have Account Access enabled to create destinations.
Connection permissions
You can grant the user role access to either All, Selected connection types, or None.
For connections, you can select one of the following permissions:
- Manage
- Create
- Edit
- View
You must be logged in as an Account Administrator or use a custom role with the Roles:Manage permission to create a custom user role.
Teams
Teams allow you to organize users into logical groups that reflect your organizational structure, including external contractors. Teams simplify permissions management across destinations and connections by letting you assign roles to groups instead of individuals.
Account Administrators and Team Managers can add users to one or multiple teams. Each team has a standard or custom role in the account and one or several destinations as well as for each connection in the destinations. For each team member, the team role extends the account permissions and group/destination permissions, including the connection permissions that the team member is assigned as an account user. For example, if your role in the destination has View permissions for all connections, and your team role has the Manage permission for all connections, then you can manage all connections in the destination.
A team can be assigned permissions to create a destination. A team is assigned the Manage Destination role for any destination it creates. A team can manage destinations and connections where the team has the Manage Destination or Manage Connection role, respectively. This includes assigning roles in the relevant resource to users and teams.
You must be logged in as an Account Administrator or use a custom role with the Roles:Manage permission to create a custom user role. Therefore, you must have an Enterprise or Business Critical plan to create and manage teams.
Teams vs. organizations
We recommend using teams when you want to ensure that only the relevant users or groups of users have access to the relevant destinations, connections or account settings. We recommend using organizations when you need to use separate security settings - SAML or SCIM.