AWS PrivateLink
You must have a Business Critical plan to use AWS PrivateLink.
AWS PrivateLink allows VPCs and AWS-hosted or on-premises services to communicate with one another without exposing traffic to the public internet. PrivateLink is the most secure connection method.
Fivetran uses PrivateLink to connect and move your data securely between our system and your AWS-hosted destination.
By default, Fivetran enables TLS on your PrivateLink connection for an extra layer of security. We recommend that you keep TLS enabled unless you know it is safe to disable it. To disable TLS, set the Require TLS when using Private Networking toggle to OFF.
If you set the Require TLS when using Private Networking toggle to OFF, Fivetran first attempts to connect over TLS. If this fails, Fivetran automatically retries the connection in clear text. You are responsible for configuring this option according to your corporate security policies.
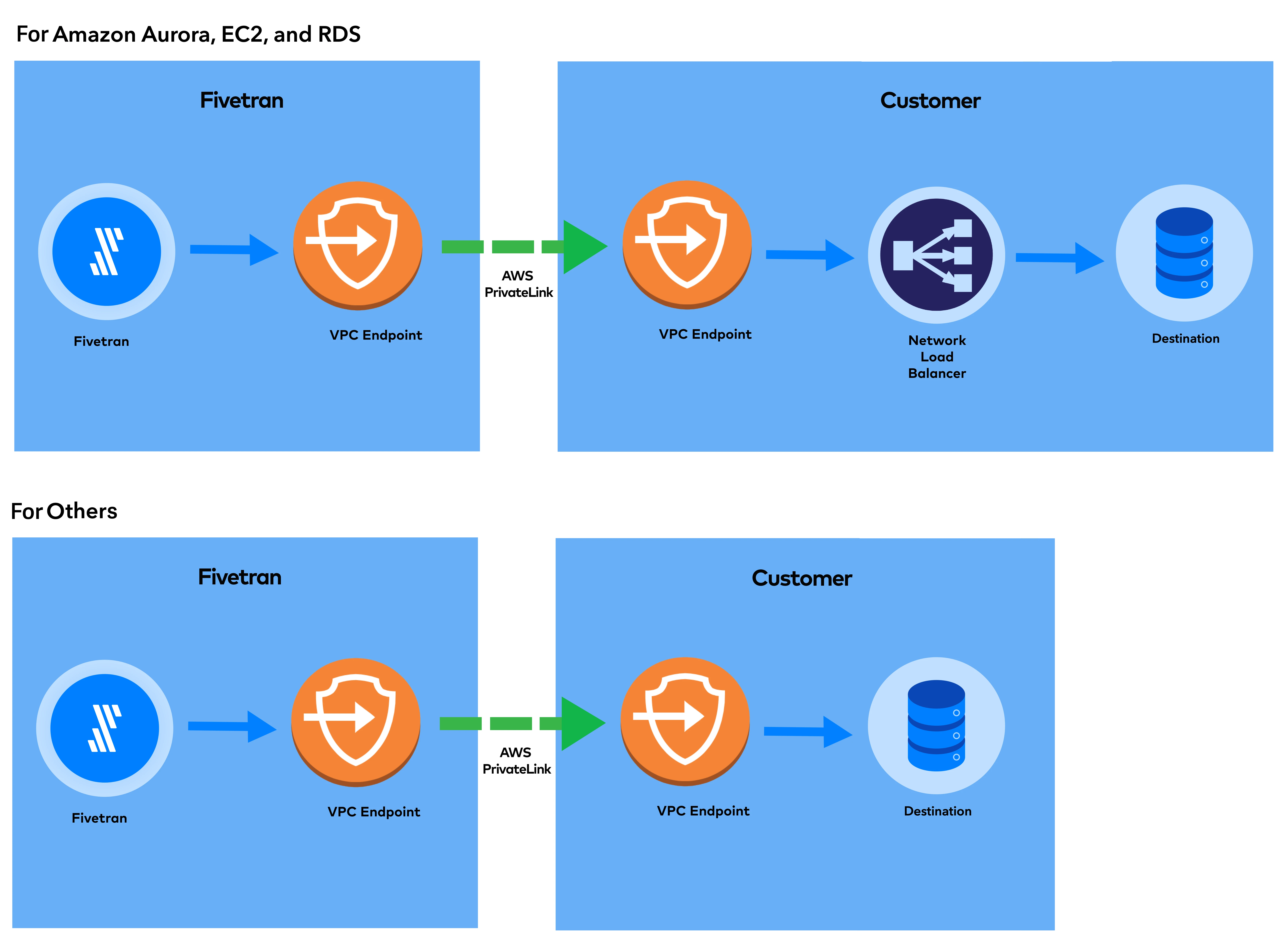
Architecture
The following graphic illustrates how Fivetran connects to a destination using AWS PrivateLink:
Supported destinations
We support AWS PrivateLink for the following AWS-hosted destinations:
- Aurora PostgreSQL
- Amazon RDS for PostgreSQL
- Aurora MySQL
- AWS MSK
- Databricks
- Generic MySQL
- Generic PostgreSQL
- Generic SQL Server
- MariaDB
- Amazon RDS for MariaDB
- Amazon RDS for MySQL
- Redshift
- Snowflake
- Amazon RDS for SQL Server
Prerequisites
To set up AWS PrivateLink, you need the following:
- An Amazon-hosted destination in one of our supported regions
- An AWS endpoint service configured for your destination
- If your destination is hosted on one of the Amazon services listed below, you must create a Network Load Balancer (NLB) in your VPC. The NLB receives requests from Fivetran and routes it to your destination.
- Amazon Aurora
- Amazon EC2
- Amazon RDS
Setup instructions
Create an NLB
On a single IP service (EC2, non-RDS destination, etc.)
To create an NLB on a single IP service, follow the instructions in AWS documentation.
While creating the NLB, you must either ensure that the availability zones of the NLB match the target availability zones or enable cross-zone load balancing.
On RDS
NLB can only route traffic to an EC2 instance, an IP address, or a Lambda function through target groups. Since RDS does not have a dedicated IP address or EC2 instance ID, you can configure the NLB in one of the following ways to route the traffic to your RDS destination:
- Using a port forwarding instance
- Using an RDS IP address
Using a port forwarding instance
Deploy an EC2 instance that is configured to do port forwarding (accepting requests from the NLB and forwarding those requests to the RDS destination). You can use the following sample script to set up the EC2 port forwarding instance:
#!/bin/bash PREVLOGFILE=/root/ip.txt # Note the below section of the code is important in the event of a server restart. if test -f "$PREVLOGFILE"; then truncate -s 0 $PREVLOGFILE echo "State file $PREVLOGFILE has been emptied" fi python -m SimpleHTTPServer 801 & # NOTE: USE PORT 801 FOR <HEALTH_CHECKS> PARAMETER BELOW echo 1 -> /proc/sys/net/ipv4/ip_forward export RDS_ENDPOINT=<<PROSPECT RDS INSTANCE ENDPOINT>> #NOTE: DO NOT INCLUDE THE <<>> CHARACTERS, NO QUOTATION MARKS. export RDS_PORT=<<PROSPECTS RDS INSTANCE PORT>> #NOTE: DO NOT INCLUDE THE <<>> CHARACTERS, NO QUOTATION MARKS. iptables -t nat -A POSTROUTING -j MASQUERADE while true do LOGFILE=/root/ip.txt Current_IP=$(dig +short $RDS_ENDPOINT | tail -n1) #NOTE: THE "/ TAIL -n1" piece is critical to ensure only the IP address of the RDS instnce is picked. if [ $LOGFILE = "" ] ; then iptables -I INPUT -i eth1 -s $Current_IP -j ACCEPT echo $Current_IP > $LOGFILE else Old_IP=$(cat $LOGFILE) if [ "$Current_IP" = "$Old_IP" ] ; then echo "IP address has not changed ($Old_IP -> $Current_IP)" else iptables -t nat -D PREROUTING -p tcp --dport 80 -j DNAT --to-destination $Old_IP:$RDS_PORT iptables -t nat -A PREROUTING -p tcp --dport 80 -j DNAT --to-destination $Current_IP:$RDS_PORT sysctl net.ipv4.ip_forward=1 iptables-save echo $Current_IP > $LOGFILE echo "IP address has changed ($Old_IP -> $Current_IP)" fi fi sleep 5 doneIf you are using Amazon Linux 2023, replace
python -m SimpleHTTPServer 801withpython3 -m http.server 801in line 6 of the script.Configure the NLB listener and target group to route traffic to the port forwarder EC2 instance.
Using an RDS IP address
When you set up an RDS destination, RDS provides an endpoint to access your destination. This endpoint resolves to an IP address. AWS does not recommend using this IP address, since it can change without notice. To work around this limitation, you can deploy a lambda function to periodically check the IP address and update the NLB target group when it changes.
To use the RDS IP address in your NLB target group, do the following:
Run the
nslookupordigcommand with the domain name of your RDS endpoint as the input to find the IP address:dig +short YOUR_RDS_DNS_ENDPOINTSet up your NLB target group with the IP address.
Deploy a lambda function to periodically perform
nslookupon the RDS endpoint to check if the IP address has changed and update the target group with the new IP address.
Set up AWS PrivateLink
The instructions in this section are not applicable to Databricks, Redshift, and Snowflake destinations. To connect these destinations using AWS PrivateLink, see their setup guides.
Endpoint service configurations are not in Fivetran’s control. Therefore, we recommend that you contact your AWS representatives to set up PrivateLink. However, we provide the following high-level instructions based on how customers typically configure their destinations.
Set up AWS Private Link with Fivetran’s assistance
Configure the NLB for each subnet (availability zone) where you want the service to be available.
Create a VPC endpoint service configuration and specify your NLB.
Make sure that you are familiar with the endpoint service considerations and you have met its prerequisites.
Safelist Fivetran’s AWS VPC Account ID (
arn:aws:iam::834469178297:root) to allow access to your VPC endpoint service.To learn how to safelist the Fivetran account ID, see AWS' documentation.
Open a Fivetran support ticket with the following details and we will complete the setup:
- Service name (VPCe) (for example,
com.amazonaws.vpce.<region_id>.vpce-svc-xxxxxxxxxxxxxxxxx) - Host name of the service/destination
- Service name (VPCe) (for example,
Activate the connection by accepting the interface endpoint connection request from Fivetran.
By default, you must manually accept the connection request. However, you can configure the acceptance settings of your endpoint service so that the connection request is automatically accepted.
Setup instructions for self-service Fivetran accounts
The self-service functionality is in Private Preview.
The self-service functionality is not available by default. Contact our support team to enable this functionality for you.
Find connection service name
Log in to your AWS account.
Configure the NLB for each subnet (availability zone) where you want the service to be available.
Create a VPC endpoint service configuration and specify your NLB.
Make sure that you are familiar with the endpoint service considerations and you have met its prerequisites.
Safelist Fivetran’s AWS VPC Account ID (
arn:aws:iam::834469178297:root) to allow access to your VPC endpoint service.To learn how to safelist the Fivetran account ID, see AWS documentation.
Make a note of your service name (VPCe) (for example,
com.amazonaws.vpce.<region_id>.vpce-svc-xxxxxxxxxxxxxxxxx). You will need it to configure Fivetran.Activate the connection by accepting the interface endpoint connection request from Fivetran.
By default, you must manually accept the connection request. However, you can configure the acceptance settings of your endpoint service so that the connection request is automatically accepted.
Configure PrivateLink connection
Log in to the Fivetran dashboard and go to the destination setup form.
In the Connection Method drop-down menu, select Connect via Private Networking.
Click + Configure a new PrivateLink connection.
Enter a Name for your PrivateLink connection.
In the PrivateLink connection service name field, enter the service name you found in Step 1.
Click Create and save. Fivetran will raise a connection request in AWS.
It might take up to 10 minutes for us to raise the connection request.
Accept connection request
Go to your AWS account.
In the top left corner, click Services, and then select VPC.
In the VPC dashboard, click Endpoint services.
Refresh the Endpoint services page to see the new connection request from Fivetran. The new connection request is in Pending acceptance state.
It might take some time for the new connection request to appear on the list.
Select the new connection request.
Go the Endpoint connections tab.
In the Actions drop-down menu, select Accept endpoint connection request.
In the Accept endpoint connection request pop-up window, enter
acceptin the text box, and then click Accept. The status of the request will change to Pending. After a few minutes, the status will change to Accepted and a Connection created message will appear in your destination setup form.
Postrequisites
To use AWS PrivateLink, you must select AWS as the Cloud service provider in the destination setup form.